Fudo ShareAccess
Simple, Secure Third-Party Access
Built as a cloud-native, browser-accessible platform, Fudo ShareAccess provides you with full control and visibility over third-party access, eliminating the need for VPNs, agents, or infrastructure changes.
Integrated with Fudo Enterprise, it enables real-time monitoring and recording, zero-trust enforcement, and AI-powered threat detection at scale.


Security
AI-Powered Third-Party Security
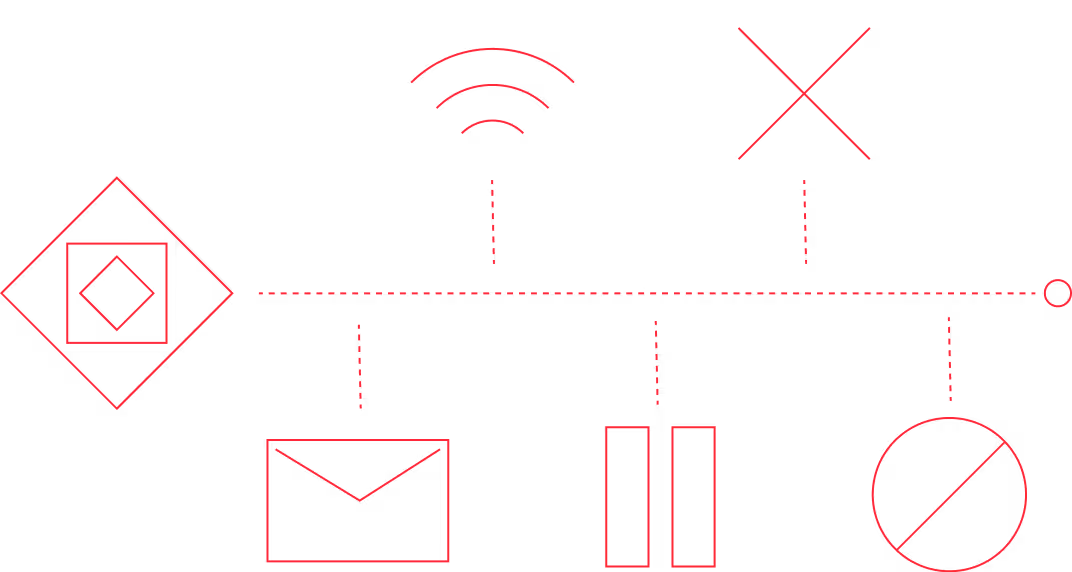
Integrated with Fudo Enterprise's AI capabilities, ShareAccess delivers comprehensive threat detection and zero-trust enforcement for all external collaborations. When security threats are detected, automated responses can be triggered, including:
- Sending an email notification
- Sending an SNMP TRAP
- Pausing the session
- Terminating the connection
- Blocking the user
Advanced Threat
Detection and Mitigation

Quantitative Behavior Model
Analyzes session data (count, duration, timing) and generates alerts for deviations from expected patterns.

Mouse Biometric Model
Analyzes 700+ features, including speed, patterns, and device type, for accurate user behavior prediction.

Keyboard Biometric Model
Extracts 100+ features like rhythm, key sequences, and force from typing dynamics.

Semantic Behavioral Model
Learns individual habits from 600+ features for accurate predictions based on keyboard input preferences.

Compliance
Comprehensive Third-Party Oversight
With complete session recording, immutable audit trails, and centralized monitoring of all external collaborations, ShareAccess delivers the visibility and control that regulatory frameworks demand for third-party access management.
Complete Third-Party Compliance & Audit

External Session Monitoring
Comprehensive monitoring of all third-party sessions with detailed recording capabilities, real-time oversight, and extensive logging for complete visibility into external collaborations.

Immutable Audit Trails
Meticulous audit trails and compliance reporting support adherence to regulatory frameworks such as GDPR, HIPAA, and PCI DSS. Detailed reports can be automatically generated, simplifying audits and reducing administrative burdens.

Third-Party Access Controls
Granular control over external user permissions with automated access approvals, time-based restrictions, and instant revocation capabilities.

Real-time Threat Detection
Advanced monitoring automatically identifies suspicious third-party activities and delivers instant alerts with automated response capabilities for proactive security.

Multi-Factor Authentication
Enforced MFA for all external users with contextual authentication that adapts security requirements based on access patterns and risk levels.

Centralized External Access Dashboard
Unified view of all third-party activities across your organization with quick navigation for incident response and comprehensive oversight.


Ease of Use
Browser-Accessible Simplicity
Our cloud-native, browser-accessible platform eliminates the need for VPNs, agents, or infrastructure changes. Experience streamlined third-party access through automated provisioning, intelligent security controls, and comprehensive administrative oversight that scales with your collaboration needs.
Enterprise-Grade Simplicity

Browser-Accessible Platform
No software installations required. Third-party users access resources directly through their web browsers with full functionality and security.

No VPN, Agents, or Infrastructure Changes
Eliminate complex VPN configurations, agent installations, and infrastructure modifications. Deploy instantly without disrupting existing systems.

Fudo Enterprise Integration
Seamlessly integrates with Fudo Enterprise for unified privileged access management across internal and external users with consistent policies.

Scalable Cloud-Native Architecture
Built for scale with cloud-native infrastructure that automatically adapts to growing partner ecosystems and expanding collaboration needs.

Full Control & Visibility
Complete oversight of all third-party activities with granular controls, real-time monitoring, and comprehensive reporting capabilities.

Zero-Trust Enforcement
Implement zero-trust principles for all external access with continuous verification, least-privilege access, and dynamic policy enforcement.

Productivity
Instant Collaboration Without Compromise
Streamline external partnerships through instant user invitations, seamless resource sharing, and intelligent access management. Transform third-party collaboration from a security bottleneck to a competitive advantage.
Frictionless External Collaboration

Instant User Invitations
Immediately invite external partners with automated onboarding workflows. Eliminate lengthy setup processes while maintaining robust security controls.

Seamless Resource Sharing
Enable secure access to enterprise resources without complex VPN configurations or firewall modifications. Partners work in their preferred native applications.

Live Collaboration Oversight
Real-time monitoring of all external collaborations with complete session visibility. Provide immediate support and maintain operational control.

Complete Session Recording
Comprehensive video recording of all external user sessions creates searchable archives for compliance documentation and security forensics.

Session Video Recording
Captures complete video recordings of all user sessions and creates searchable session archives that support compliance documentation, security forensics, and productivity analysis.

Login/Active Time-Based Reporting
Tracks detailed login patterns, session durations, and active time metrics to analyze workforce engagement and productivity patterns.
Testimonials
Need comprehensive internal privileged access management?
Check out Fudo Enterprise for AI-powered behavioral analysis and intelligent PAM.
01
Advanced AI behavioral analysis with 1,400+ behavioral features
02
Complete session recording and administrative control
03
Enterprise-grade compliance with AI automation
04
High-availability architecture with failover clusters
05
Simple agentless deployment




























