USe cases
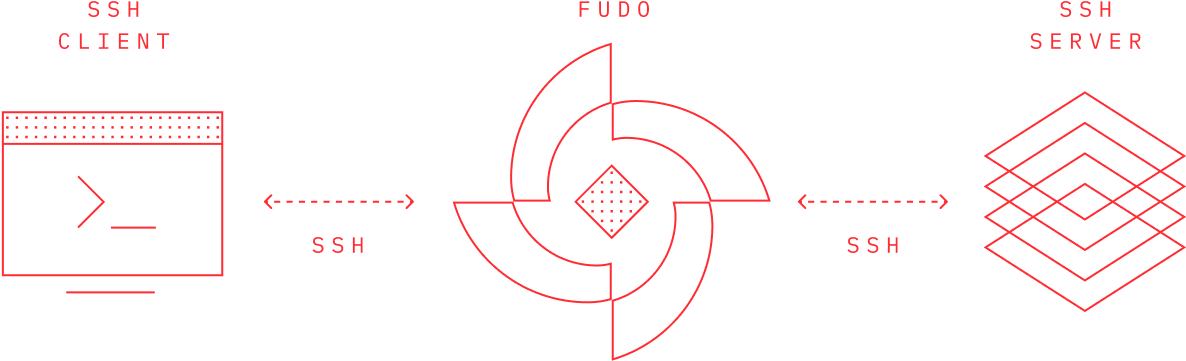
PAM for Terminals (SSH)
Secure SSH Access with Comprehensive Terminal Control
Fudo Enterprise provides advanced privileged access management for SSH terminal environments through intelligent behavioral monitoring and real-time threat detection. Our solution delivers transparent SSH session oversight, automated compliance documentation, and seamless integration with existing Unix/Linux infrastructure - without requiring agents or system changes.

Challenge
SSH Terminal Vulnerabilities Create Critical Security Gaps
SSH terminal access presents significant security risks through compromised keys, privilege escalation, and limited session visibility. Traditional SSH security depends on key management and perimeter controls that cannot detect malicious activities or monitor privileged user behavior within active terminal sessions.
Key Issues
- Compromised SSH keys enable undetected system access
- Insufficient visibility into command execution and system modifications
- Privilege escalation through legitimate SSH connections
- Compliance challenges in terminal session auditing
- Manual key management creates operational security risks
Solution
Intelligent SSH Access Control
Fudo Enterprise transforms SSH security through comprehensive terminal session management that combines AI-powered analysis with real-time behavioral monitoring. Our platform provides complete visibility and control over SSH sessions while preserving native terminal functionality and administrative efficiency.

Features
Advanced SSH Security & Terminal Control

Command-Level Behavioral Analysis
AI-powered monitoring analyzes SSH session patterns, command sequences, and system interactions. Automated detection identifies anomalous terminal behavior and unauthorized command execution.


Complete Session Recording
Full terminal session recording with searchable command logs and keystroke capture. Comprehensive archives support compliance requirements, security investigations, and operational analysis.

Real-Time Terminal Monitoring
Live session visibility enables administrators to observe active SSH connections, monitor command execution, and intervene when security policies are violated.

Transparent SSH Proxy
Agentless deployment integrates seamlessly with existing SSH infrastructure. Users connect through standard SSH clients while all terminal sessions flow through Fudo's intelligent security layer.


Automated Compliance Reporting
Generate detailed compliance reports documenting terminal access, command execution, and privilege usage. Comprehensive logging supports regulatory frameworks and security investigations.


SSH Key Management Integration
Automated SSH key rotation, secure key distribution, and centralized key lifecycle management eliminate manual key handling while maintaining seamless terminal access.

Benefits
Measurable SSH Security Improvements
Enhanced Threat Detection
AI-powered behavioral analysis detects malicious command patterns, privilege abuse, and unauthorized system modifications that traditional SSH security cannot identify.
Comprehensive Auditing
Complete session recording and command logging satisfy regulatory requirements for privileged access documentation and forensic analysis capabilities.
Operational Efficiency
Unified terminal access control reduces administrative complexity while providing granular oversight of user permissions, command execution, and system access patterns.
Native Client Compatibility
Support for standard SSH clients including PuTTY, OpenSSH, and terminal emulators ensures transparent user experience without workflow disruption.
Common SSH Terminal Security Scenarios
Integration
Seamless SSH Infrastructure Integration
Fudo Enterprise integrates with existing Unix/Linux environments, identity management systems, and SSH infrastructure without requiring system modifications or client software installation. Support for standard SSH protocols ensures compatibility across diverse terminal environments.
- LDAP and Active Directory authentication
- SSH key management systems
- Jump host and bastion server integration
- SIEM and security monitoring tools
- Compliance reporting systems
Explore Related PAM Solutions
- Advanced AI behavioral analysis with 1,400+ behavioral features
- Complete session recording and administrative control
- Enterprise-grade compliance with AI automation
- High-availability architecture with failover clusters
- Simple agentless deployment